
Phishing Scams: Redundant and Predictable but Still Trendy – How to Stay Safe
(suomeksi alla)
Every time a major phishing attack hits the headlines, news outlets make it sound so surprising and unprecedented. But for those of us working closely with data security and IT, the storyline falls flat because we know: all phishing attacks follow the same structure. At its core, phishing is the type of cybercrime that preys on human psychology rather than exploiting technical vulnerabilities. The anatomy of a typical phishing attack follows a predictable pattern:
Bait, Hook, Catch.
It all starts with the phisher collecting information about their target. This is crucial but easy. It can be as simple as pretending to be the banking service the victim is using.
In a country like Finland, where a few banks dominate the market, an attacker can send the same lure to everyone, confident that it will eventually land on someone who uses the bank they are pretending to represent. It goes without saying that attackers will mimic the branding, language, and tone of the service they’re impersonating. The message is almost always about something that needs to be done urgently, followed by a link to the phishing website. Even the URL looks authentic at first glance, but the moment you start typing your personal information, it goes straight into the attacker’s database.
The catching and harvesting are quite straightforward. Once a third party gets access to your accounts, the rest of the story turns quite bleak. The data can either lead to further phishing through using your credibility as the new bait (especially if this attack is directed towards a company) or if the data itself can be used against you, it would be either exploited instantly or sold on the dark web in bulk.
Let’s skip to the good part:
How to avoid phishing attacks?
This is an issue best addressed through prevention and training. The rule goes as follows: Unless you’re the one that initiated contact, never provide sensitive information like your social security number or account information including the surname/reference. When a legitimate service contacts you, they usually ask you to log into your account independently, without including any links in the notifying message or email. If the caller or the content of the communication makes you feel uneasy or pressured, it is highly recommended to take a step back and remember that no legitimate customer service will try to instill panic in you.
Unfortunately, the phishing scams have evolved to look like the real thing, which means even high levels of awareness might not be enough.
Spear Innovations offers a multitude of training courses if you are interested in learning more on this subject.
Debunking Myths
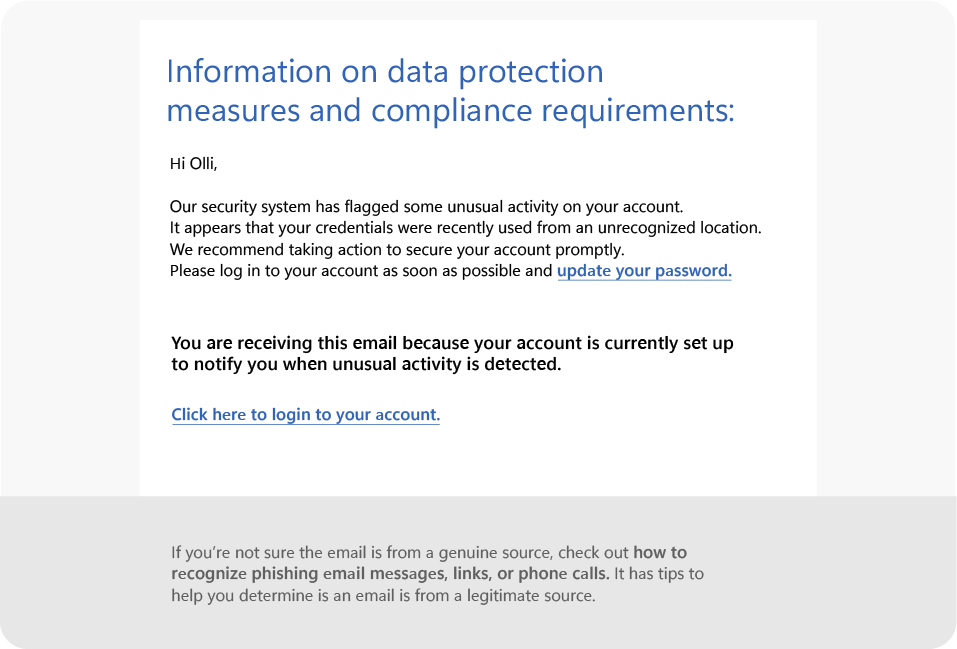
A lot of the advice out there is something along the lines of “Know what a phishing scam looks like”; which is counter productive because phishing scams, as shown in the example do look like the legitimate services. Having long passwords, having complex passwords and changing passwords often doesn’t matter, when you are typing them into the phishing website. Weak MFAs like authenticator apps or OTP solutions provide no real protection from phishing. Any detail you enter at a phishing site can be misused as quickly as you enter them.
It’s easy to say “Don’t give your information to an unsecured site”, but most phishing sites nowadays are secured and have the https:// so it’s very difficult to distinguish them from the original website. These old tricks could have been useful in the past, but nowadays criminals use AI based tools to craft their lure. Relying on intuition alone is no longer as efficient.
The ultimate phishing resistant technology on the market right now is FIDO2.
If you don’t know what FIDO2 stands for it’s Fast Identity Online and it works through providing a hardware security solution for a cybersecurity problem. The technology was designed to combat phishing. And provide an easy and secure way to login without the chance of man-in-the-middle attacks.
How does FIDO2 work?
FIDO2 security keys introduce a crucial factor into the online authentication process: physical presence. When you log into your accounts, you’re required to physically interact with the security key by pressing its button. This means that no one can access your accounts unless they have physical possession of your key.
In essence, FIDO2 security keys eliminate the possibility of intermediaries interfering between the server and your computer. Even if someone manages to intercept the communication, they would still need your explicit permission, signaled by the button press on your specific key. This approach ensures that your online accounts remain secure, with unauthorized access effectively blocked unless someone physically possesses your security key. It’s a significant step towards enhancing online security and safeguarding your digital identity.
You can also learn more about FIDO2 through our website: www.fido2.fi
Tietojekalasteluhuijaukset: Ennalta-arvattavia, mutta silti trendikkäitä – Miten pysyä turvassa?
Aina kun suuri tietojenkalasteluhyökkäys on otsikoissa, uutistoimistot saavat sen kuulostamaan niin yllättävältä ja ennennäkemättömältä. Meille, jotka työskentelemme tiiviisti tietoturvan ja tietotekniikan parissa, tässä ei ole mitään uutta, koska tiedämme, että kaikki kalasteluhyökkäykset noudattavat samaa rakennetta. Pohjimmiltaan tietojen kalastelu on tietoverkkorikollisuutta, joka perustuu pikemminkin ihmisen psykologiaan kuin teknisten haavoittuvuuksien hyödyntämiseen. Tyypillisen kalasteluhyökkäyksen anatomia noudattaa ennalta arvattavaa kaavaa:
Syötti, koukku, saalis.
Kaikki alkaa siitä, että tietojenkalastelija kerää tietoja kohteestaan. Tämä on tärkeää mutta helppoa. Se voi olla niinkin yksinkertaista kuin teeskennellä olevansa uhrin käyttämä pankkipalvelu.
Suomen kaltaisessa maassa, jossa muutama pankki hallitsee markkinoita, hyökkääjä voi lähettää saman houkuttimen kaikille luottaen siihen, että se lopulta osuu johonkin, joka käyttää pankkia, jota hän esittää edustavansa. On sanomattakin selvää, että hyökkääjät jäljittelevät tekaistun palvelun brändiä, kieltä ja äänensävyä. Viestissä kerrotaan lähes aina jostain kiireellisesti hoidettavasta asiasta, ja sen jälkeen on linkki tietojenkalastelusivustolle. Jopa URL-osoite näyttää ensi silmäyksellä aidolta, mutta heti kun alat kirjoittaa henkilökohtaisia tietojasi, ne siirtyvät suoraan hyökkääjän tietokantaan.
Pyynti ja sadonkorjuu ovat melko yksinkertaisia. Kun kolmas osapuoli pääsee käsiksi tileihisi, tarinan loppuosa muuttuu varsin synkäksi. Tiedot voivat joko johtaa uuteen tietojen kalasteluun käyttämällä luottamustasi uutena syöttinä (varsinkin jos hyökkäys kohdistuu yritykseen) tai jos tietoja voidaan käyttää sinua vastaan, niitä hyödynnetään välittömästi tai myydään pimeässä verkossa irtotavarana.
Siirrytäänpä sitten hyvään osuuteen:
Miten välttyä tietojenkalasteluyrityksiltä?
Tähän ongelmaan on parasta puuttua ennaltaehkäisyn ja koulutuksen avulla. Sääntö kuuluu seuraavasti: Älä koskaan anna arkaluonteisia tietoja, kuten sosiaaliturvatunnusta tai tilitietoja, mukaan lukien sukunimi/viittaus, ellet ole itse aloittanut yhteydenottoa. Kun laillinen palvelu ottaa sinuun yhteyttä, se yleensä pyytää sinua kirjautumaan tilillesi itsenäisesti ilman, että ilmoitusviestissä tai sähköpostiviestissä on mitään linkkejä. Jos soittaja tai viestin sisältö saa sinut tuntemaan olosi levottomaksi tai painostetuksi, on erittäin suositeltavaa ottaa askel taaksepäin ja muistaa, että mikään laillinen asiakaspalvelu ei yritä lietsoa sinuun paniikkia.
Valitettavasti tietojenkalasteluhuijaukset ovat kehittyneet näyttämään aidoilta, mikä tarkoittaa, että korkeakaan tietoisuus ei välttämättä riitä.

Spear Innovations tarjoaa lukuisia koulutuskursseja, jos olet kiinnostunut oppimaan lisää tästä aiheesta.
Myyttien kumoaminen
Monet neuvot ovat tyyliltään: ”Tiedä, miltä kalasteluhuijaus näyttää”, mikä on haitaksi, sillä kuten esimerkissä näkyy, tietojenkalasteluhuijaukset näyttävät laillisilta palveluilta. Salasanan pituudella tai monimutkaisuudella ja salasanojen usein vaihtamisella ei ole väliä, kun kirjoitat ne kalastelusivustolle. Heikot MFA:t, kuten autentikointisovellukset tai OTP-ratkaisut, eivät tarjoa todellista suojaa tietojenkalastelulta. Kaikkia kalastelusivustolle syöttämiäsi tietoja voidaan käyttää väärin yhtä nopeasti kuin syötät ne.
On helppo sanoa: ”Älä anna tietojasi suojaamattomalle sivustolle”, mutta useimmat kalastelusivustot ovat nykyään suojattuja ja niissä on https://, joten niitä on hyvin vaikea erottaa alkuperäisestä sivustosta. Nämä vanhat temput saattoivat olla hyödyllisiä aiemmin, mutta nykyään rikolliset käyttävät tekoälyyn perustuvia työkaluja houkutustensa suunnitteluun. Pelkkään intuitioon luottaminen ei ole enää yhtä tehokasta.
FIDO2 on tällä hetkellä markkinoiden paras tietojenkalastelunkestävä teknologia.
Jos et tiedä, mitä FIDO2 tarkoittaa, se on Fast Identity Online, ja se toimii tarjoamalla laitteiston turvaratkaisun kyberturvallisuusongelmaan. Teknologia on suunniteltu tietojenkalastelun torjuntaan ja tarjoamaan helppo ja turvallinen tapa kirjautua sisään ilman välikäsien hyökkäyksiä.
Kuinka FIDO2 toimii?
FIDO2-avaimet tuovat verkkotunnistusprosessiin ratkaisevan tekijän: fyysisen läsnäolon. Kun kirjaudut tileillesi, sinun on oltava fyysisesti vuorovaikutuksessa turva-avaimen kanssa painamalla sen painiketta. Tämä tarkoittaa, että kukaan ei pääse tileillesi, ellei hänellä ole avainta fyysisesti hallussaan.
Pohjimmiltaan kyse on siitä, että FIDO2-avaimet poistavat mahdollisuuden, että välittäjät voisivat olla palvelimen ja tietokoneen välissä. Vaikka joku onnistuisikin sieppaamaan viestinnän, hän tarvitsisi silti nimenomaisen lupasi, joka ilmaistaan painamalla turva-avaimen painiketta. Tämä lähestymistapa varmistaa, että verkkotilisi pysyvät turvassa, ja luvaton pääsy on tehokkaasti estetty, ellei joku fyysisesti hallitse turva-avainta. Tämä on merkittävä askel kohti verkkoturvallisuuden parantamista ja digitaalisen identiteettisi turvaamista.
Voit myös tutustua FIDO2:een tarkemmin sivustollamme: www.fido2.fi